Transfer security
The peace of mind of keeping your files fully protected
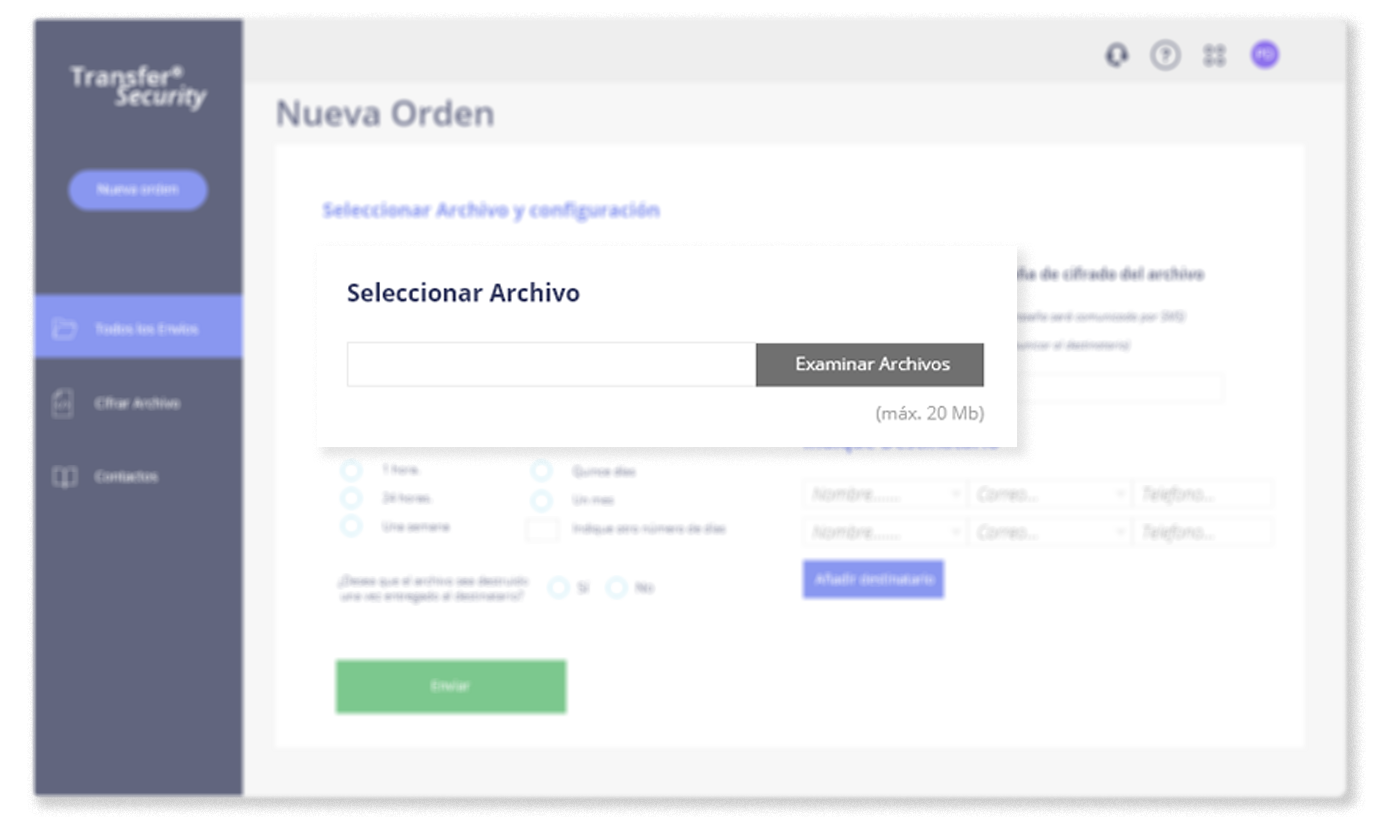
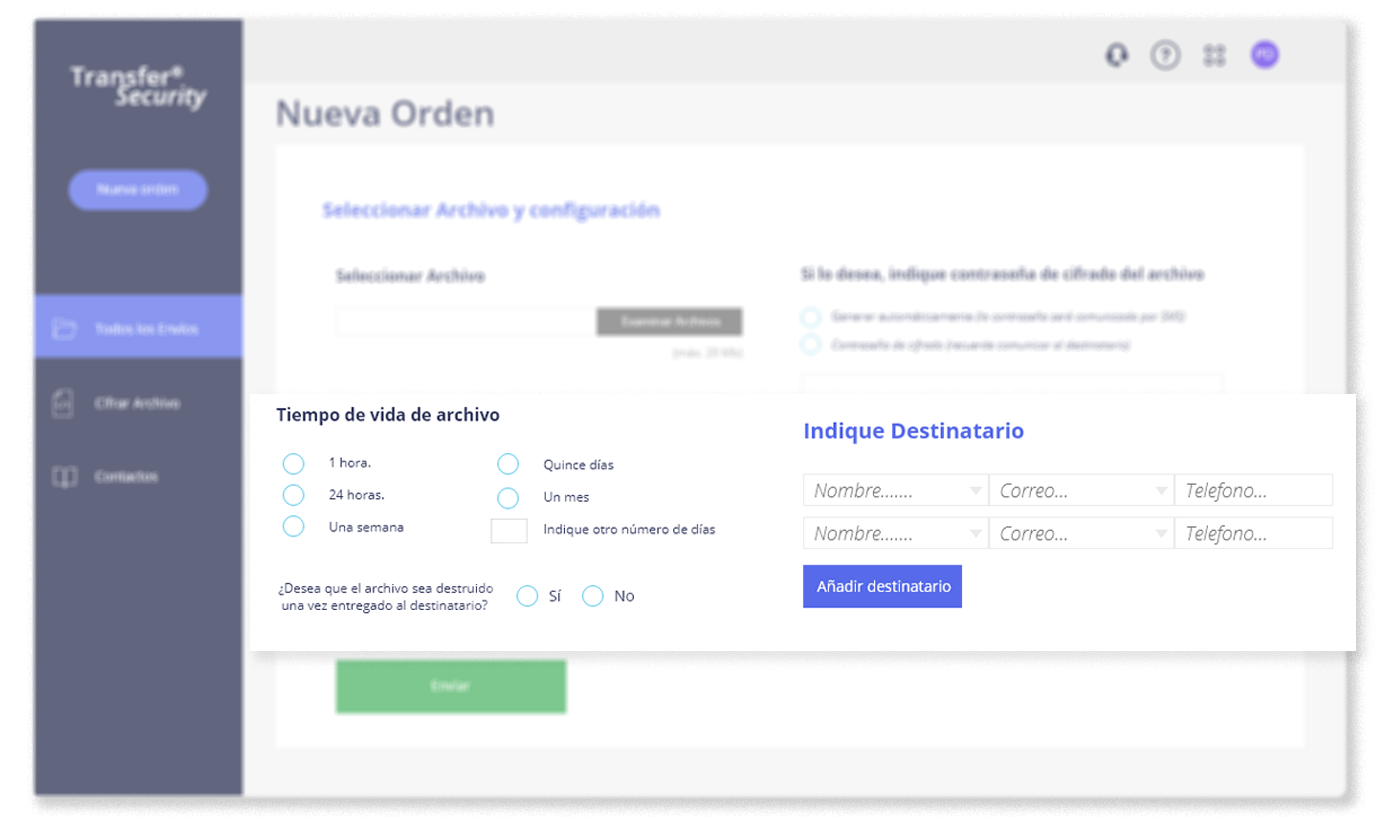
How does it work?
1End-to-end encryption
Symmetric encryption with AES (Advanced Encryption Standard) algorithm. Key length of 256 bits.2Automatic file expiration and deletion.
In addition to the possibility of incorporating a maximum number of failed access attempts. After the fifth failed attempt, the file is locked.3RGPD compliance.
This service allows compliance with the obligations imposed by current legislation on data protection, to those responsible and in charge of data processing. In compliance with RGPD and LOPD.4Easy to use and configure.
No installation required. Transfer Security's modern and intuitive user interface requires little, if any, training and can be customized based on both IT and non-IT requirements.5Platform and API
Solution can be integrated into any process or third party software. Available in platform and API version.
Do you want to be a PARTNER?
Become a Transfer Security reseller and offer your customers the best secure file transfer tool on the market.